Hacking Security Feeds for Fun (and CVEs)
If you’ve ever found yourself in a movie theater, you’ve undoubtedly seen, time and again, one of Hollywood’s favorite spectacles: the dramatically unrealistic hacking scene. Hollywood has long (ab)used hacking scenes, particularly those involving security feeds, with little concern for technical accuracy (s/o to Mr. Robot’s technical advisors, we love you). Yet certain elements are ever-present: the computer genius, forever depicted as insecure, rebellious or plain weird, cracks the system in just ten seconds, setting the stage for the moment every single screenwriter seems to live for, the iconic (and infamous) I’M IN!
Is hacking into security cameras that easy? The quick answer is no. The detailed answer is complicated.
Hacking into a bank’s dedicated, off-the-internet video feed is, thankfully (and hopefully), not a simple task. But what about the low hanging fruits?
Within the infosec community, there’s a widespread belief that IoT devices lack basic security measures. Well, let’s test this belief!
All research credit goes to our research group, @IoTaK0s <3.
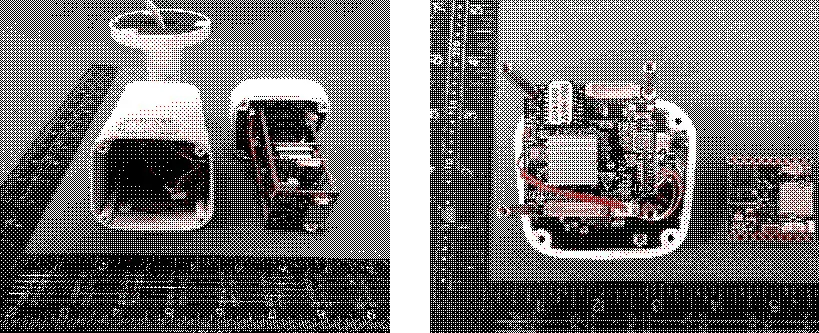
The target
Our chosen device is the EXVIST ZSD8WNH16A camera. We chose this camera because it has both advanced features (human detection, IR, 4K resolution) and publicly available documentation.